The LightHouse
Blog

GoDaddy Issues?
Godaddy offers small businesses a excellent entry level, email & website option. But as your business grows we have seen at least 5 common issues that start to hurt. We outline those 5 common items, explain why they happen and what you can do to protect your business.
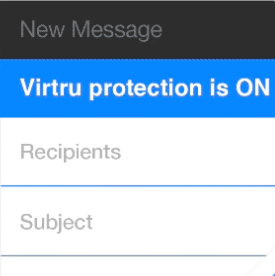
Virtru Offers Simple Encrypted Email Services
Virtru Offers Simple Encrypted Email Services We are always on the look out to keep our clients protected from hackers and digital thieves and were pleasantly surprised while recently using Virtru's encrypted email service. I personally use to send...

Hackers Find Fresh WordPress Sites Within 30 Minutes
Hackers Find Fresh WordPress Sites Within 30 Minutes Hackers are now able to pinpoint fresh WordPress installs and slip Trojans into them. Vital Help Desk managed Wordpress service will make sure your website stays secure. Last week our team...
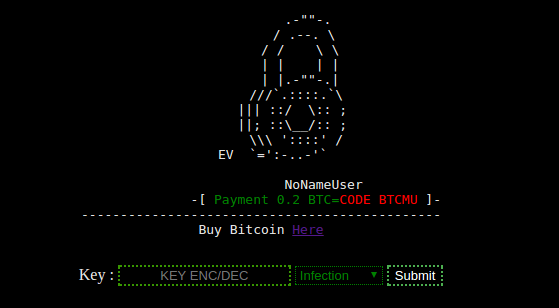
Ransomware Targeting WordPress – An Emerging Threat
Ransomware Targeting WordPress - An Emerging Threat There are new ransomware variants that are starting to target unprotected WordPress sites. Vital Help Desk managed Wordpress hosting keeps you protected. Recently, the Wordfence team has...

Last Chance, “Mobilegeddon” is coming on April 21 – Are You Mobile Optimized?
Recently Google announced, Starting April 21, they will be expanding the use of mobile-friendliness as a ranking signal. This change will affect mobile searches in all languages worldwide and will have a significant impact in your search results.
This means we all need to prepare for (cue dramatic music) MOBILEGEDDON! Mobile optimized websites/pages are going to be a part of Google’s Ranking Signal and certainly will affect mobile searches after the update rolls out.

Mobile Flightlight Apps steals your data
Mobile Flightlight Apps steals your data As always Vital Help Desk is back with important security alerts which we are concerned about and want to help spreading awareness between our clients, family and friends. We are completely shocked to...

Todoist Review – how to get things done (GTD)
Todoist Review – how to get things done (GTD) Are you a person who repeatedly writes down daily tasks or to-do lists? Smartphone’s are taking task manager to-do things one step further with so many apps to choose from. But not all solutions are equal. We...

Toggl Review – Simple Time Management Tool
Toggl Review – Simple Time Management Tool Toggl is one of the simplest time management tools. Wherever you might be, Web, Desktop or even on Mobile, it’s just a single click away from tracking your work time. No matter being online or offline, it syncs...

Important security tips on fighting ransomware
Important security tips on fighting ransomware An important part of our job as a secure hosting provider is keeping our Florida clients informed of new threats. And the one we’re most concerned about is ransomware. Here’s a quick breakdown of what this...

“Zero day” vulnerability in IE – what’s at risk
"Zero day" vulnerability in IE – what’s at risk You may have seen recent alerts about the “Zero Day” vulnerability in Internet Explorer. As part of our work as a secure hosting provider, we wanted to share some quick points about the threat: Windows OS...
Follow us
